Microsoft has issued a warning about new Web3 risks, including “ice phishing” attacks. There appears to be a spike in the use of blockchain and DeFi technology. As a result, the need to include security into the decentralised web while it is still in its infancy has grown.
The Microsoft 365 Defender Exploration Workforce identified a number of new ways for malicious actors to engage in cybercrime. They try to dupe crypto currency users into handing up their private cryptographic keys in order to conduct unlawful fund transfers.
Phishing attacks in blockchain
Christian Seifert, principal research manager at Microsoft’s Security and Compliance department, commented on blockchain crimes. He stated, “One aspect that the immutable and public blockchain provides is total clarity, so an assault can be witnessed and investigated after it occurs.” “It also allows assessment of the financial impact of attacks, which is quite challenging in traditional web2 phishing attacks.”
Theft of the keys could be accomplished in a variety of ways. It involves posing as wallet software, infecting victims’ devices with malware, and typosquatting legitimate smart contract front ends.
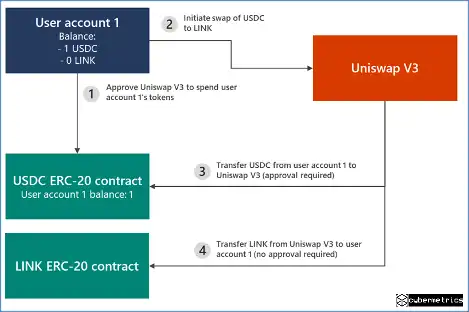
The spender can access the funds after the approval transaction has been signed, filed, and mined. Seifert went on to say more. He went on to say that in the instance of an ‘ice phishing’ attack, the attacker can gather approvals over time and then suddenly drain all of the content of the victim’s wallets.
The high-profile attack of Ethereum-based DeFi platform BadgerDAO in early December 2021 was one such example of ice phishing.
Badger D.A.O. attack
Badger is a DeFi protocol that allows users to earn interest on Bitcoin deposits, and it was released on the Ethereum mainnet in December 2020. Users deposit wrapped Bitcoin into vaults, which earn income using various yield farming tactics. Badger has a total volume of 978 million U.S. dollars locked up right now.
A series of fraudulent transactions happened on December 2nd, 2021, resulting in the loss of cash from Badger users. The adversary was able to drain $121 million in money using a maliciously injected snippet and a compromised API key. Following the exploit, Badger engineers collaborated with cyber security firm Mandiant to examine the event, and the following preliminary report was produced.
On December 2nd, 2021, a maliciously injected snippet given by Cloudflare Workers resulted in a phishing incident. The worker script was deployed by the attacker using a hacked API key that was created without the knowledge or permission of Badger engineers. The attacker(s) utilised this API access to inject malicious code into the Badger application on a regular basis, affecting just a small portion of the user base.
The software was written in such a way that it would intercept Web3 transactions from wallets with a certain balance. The attackers will then inject a request to transfer the victim’s tokens to a handle they prefer.
The web3 stack is still in its infancy, posing hazards to users. The quantity of money stolen in this ‘ice phishing’ attempt was unparalleled. On the Rekt leaderboard of most expensive crypto hacks, it now ranks sixth. It’s worth noting that the funds taken came primarily from user wallets, not from Badger D.A.O.’s smart contracts.
While Badger conducted a postmortem and took steps to safeguard infrastructure and unpause contracts6, similar assaults are likely to occur. Fortunately, because blockchain transactions are public, these types of assaults may be identified as early as possible and automatically.
Endnote
To counteract risks to blockchain technology, Microsoft advises people to evaluate and audit smart contracts for appropriate incident response or unanticipated emergency capabilities and reassess and revoke token permissions on a regular basis.

