History of Cuba Ransomware
Cuban Ransomware, which has a history of being released in the year 2019, are back again after three years. The Computer Emergency Response Team(CERT), based in Ukraine has warned against the ransomware’s return in some of the critical networks of the country.
How the researchers found they are back?
This Cuban variant has relatively silent activity compared to other variants such as Avaddon, DoppelPaymer, Conti, and REvil. All these variants began calmly through 2019 but elevated gradually their actions since 2021, and are back again in2022 with more destruction. Seeing their widespread destruction power FBI published a Cuba ransomware advisory notice in the December of 2021.
Even the CERT based in Ukraine kept a close eye on the new crest of phishing emails in the name of the Press Service of the Armed Forces in Ukraine.

The Hacking process
All the emails being sent had a similar pattern where the prospects were required to click on an encapsulated link, which lands on the threat actor’s page.
Here the third-party web page; reportedly asks the user to download a portable document format “Haka3_309.pdf”. After this step, the recipient receives a pop-up asking to update their pdf software before reading this document. After the update is done, this foreign website asks its users to press a “DOWNLOAD” pop-up to download an executable file named “AcroRdrDCx642200120169_uk_UA.exe” spoofing to be an Adobe Acrobat installer app. But, when the user will run this file it will install a DLL file, “rmtpak.dll”. Execution of this installed file will activate one of the Cuban Ransomware’s trademark malware called “ROMCOM RAT”.
This ROMCOM variant of malware was first found by researchers in August 2022 on the Palo Alto Networks. Researchers named this new malware then “Tropical Scorpius”.
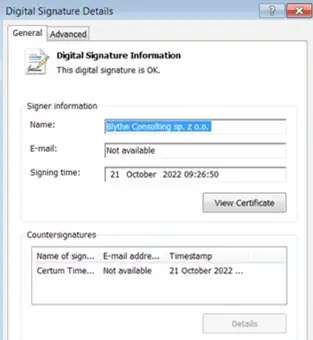
The main task of this Cuban Variant:
The main task of this malware is to assist the hackers in manipulating the document operations on the host machine, spawn spoofed processes, start reverse shell scripts, and of course the most performed- steal data from the host node.
Some additional details:
Researchers have lately found this Ransomware to have been used against the Ukraine Army. The malicious files used in the attacks have valid digital signatures and certificates.
The victims of this malware are spread in the areas like Brazil, the Philippines, and the US.
Recently in the last month, the attackers hit the small Balkan country of Montenegro and asked for a release of 1 Crore Dollars in return.
Although these attacks are seen as geo-political trends, the attackers are least interested in taking sides with Ukraine or Russia.
For more such technical news and articles stay tuned to cybermetrics.eu.

