Russia has many state-sponsored hacking organizations, APT29 has lately been very active over the week. It has started a new phishing movement around the globe. It uses some top-notch file sharing and storage devices like DropBox and Google to drop malicious payloads on vulnerable systems. Researchers have found these frequent attacks as a heavy threat to the businesses and diplomats around the world. As, these legitimate sharing drives have been lately very popular around the Corona outbreak, making them the sole flag-bearer of shared files. The ubiquitary nature of these platforms has made the cybersecurity teams on alert as they are frequently being targeted by the APT.
Who are APT29?
APT29(advanced persistent threat 29), ‘Cozy Bear’, or ‘Nobelium’, or ‘Cloaked Ursa’, or ‘The Dukes’ is a Russian cyber espionage collective, sponsored by the Russian government. It targets mostly the Western diplomatic world to collect strategic pieces of information for Russia.
Click here to know more about the latest Russian ransomwares and malwares.
The History
It has carried out most of the infamous hacks in the past. Such as the hireling of the US Democratic National Committee(DNC), 2016, and the SolarWinds supply chain hacks of 2020. After these persistent compromises, the US and UK have publicly announced this group’s connection to the Russian Foreign Intelligence Service(SVR).
In the past also the malware used by them was difficult to crack due to their use of official legitimate services and encryption.
Recent Targets
The recent hacks carried out by this group were on numerous Western Diplomats between May and June of 2022. They specifically lured the foreign embassies of Portugal and Brazil for an upcoming meeting with an ambassador.
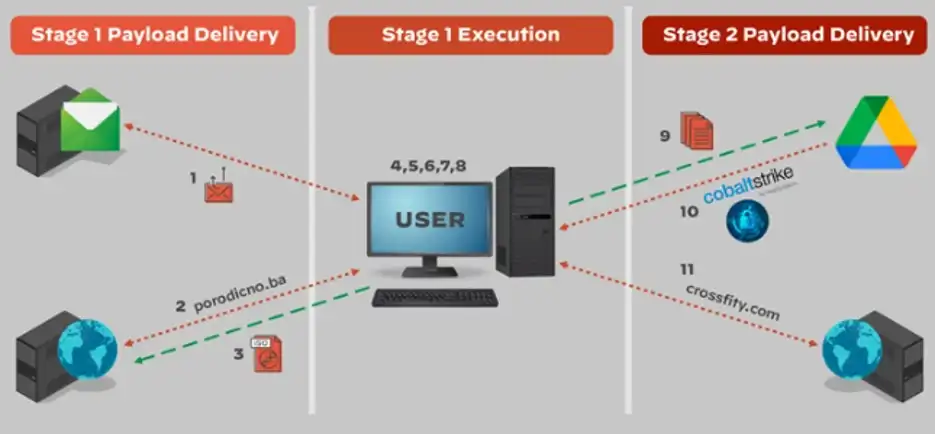
Their way of targetting the victims is the same in both cases, where they sent ‘Agenda.pdf’ documents and phished the information towards the malicious HTML file, EnvyScout.
The target network also has another file serving as the payload for the victim’s device, known as the Cobalt Strike payload.


EnvyScout -Agenda.html, a malicious HTML file
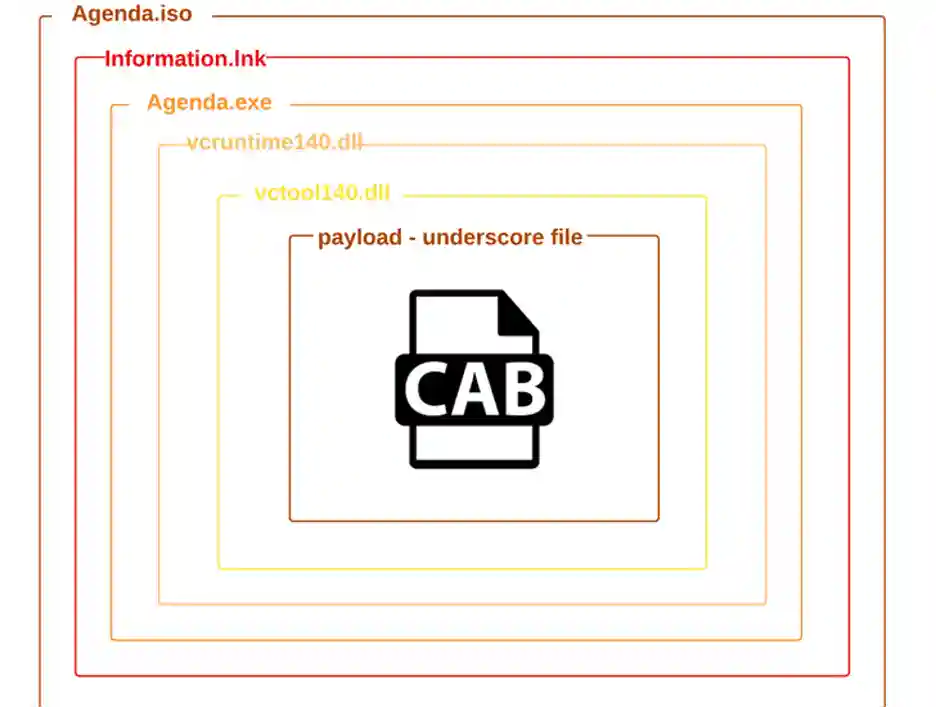
The latest campaigns carried out by the APT use a malicious HTML file, that further corrupts the compromised target, with the actor’s implant of choice. Basically, the hackers use Agenda.html to write another file with the same name on the compromised drive location, but having an iso extension.
After clicking this bait the victim gets trapped as the .NET executable file, that is the main payload gets downloaded and corrupts the drive stealing all the confidential data.
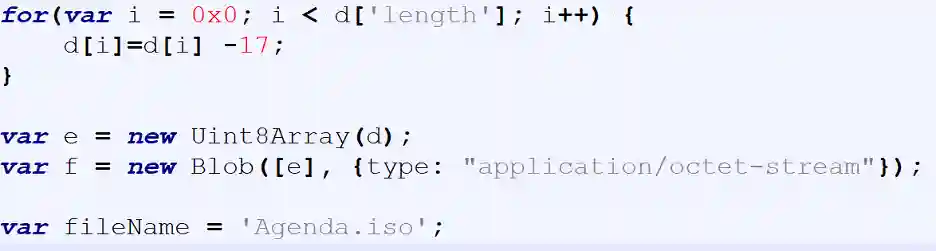
The embedded payload is cracked out by reducing 17 from each value as shown below:
Protection and Mitigation against the Attacks
Palo Alto Network Customers can use the following products that can protect against any compromisation:-
- A cloud-based hazard test called WildFire recognizes the specimens in the drive as malicious or good.
- Industry-First XDR, Cortex XDR uses AI to stop ransomware attacks.
- Advanced URL filtering and DNS Security system identifies the vicious stuff on the drive or the networks.
If you think you have been attacked then a call can be made on any of the following numbers below:
- APAC: +65.6983.8730
- EMEA: +31.20.299.3130
- Japan: +81.50.1790.0200
- North America Toll-Free: 866.486.4842
Found this post interesting then please share it with people who can be helped with this information. Please follow cybermetrics.eu to support us. Signup for our weekly news feed.
Written By: Ankita Anand
Editor: Robin

