In the year 2019, the Cuba ransomware was released. Compared to other operations such as REvil, Avaddon, Conti, and DoppelPaymer, it had a relatively quiet activity. They began slowly, but in 2020 and 2021, they began to escalate their activities. As a result of the increased activity, the FBI issued a Cuba ransomware advisory in December 2021.
To get early access to business networks and encrypt devices, the ransomware operation is now leveraging Microsoft Exchange vulnerabilities. The ransomware gang is known as UNC2596. The malware itself is known as COLDDRAW, according to cybersecurity firm Mandiant.
Cuba is the most frequent name for malware. Researchers indicate that the Cuba operation predominantly targets the United States, followed by Canada, according to a new analysis by Mandiant.
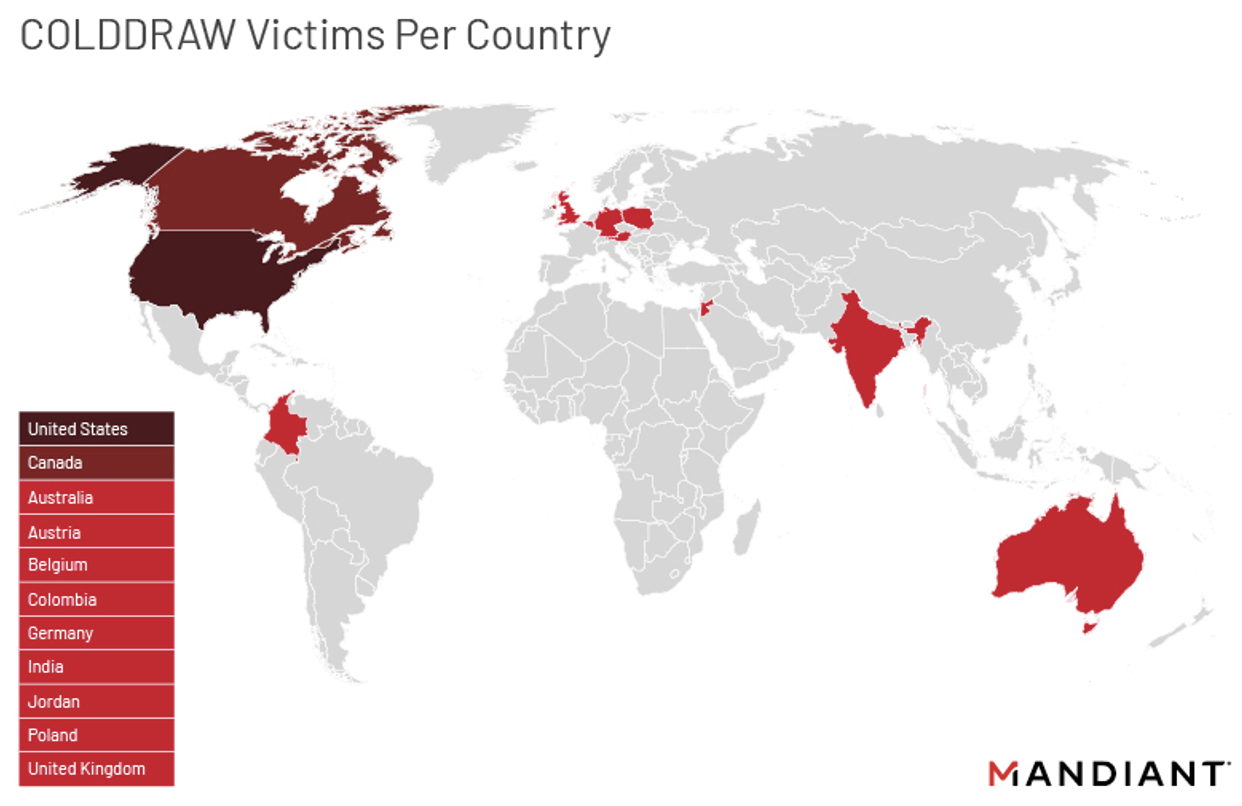
Exploited by Cuba Ransomware
The Cuba ransomware also exploited Microsoft Exchange vulnerabilities. “These threat actors have exploited webshells to load the TERMITE in-memory dropper during intrusions. Multiple backdoors and built-in Windows tools are used in the subsequent action,” according to Mandiant.
Including ProxyShell and ProxyLogon, UNC2596 leveraged these access points as early as August 2021. They used the access points to set up web shells, RATs, and backdoors to gain a foothold on the target network. Some of the backdoors placid include Cobalt Strike and the NetSupport Manager remote access program. However, the gang also employs their own malware such as ‘Bughatch,’ ‘Wedgecut,’ and ‘eck.exe’ tools, as well as Burntcigar’.
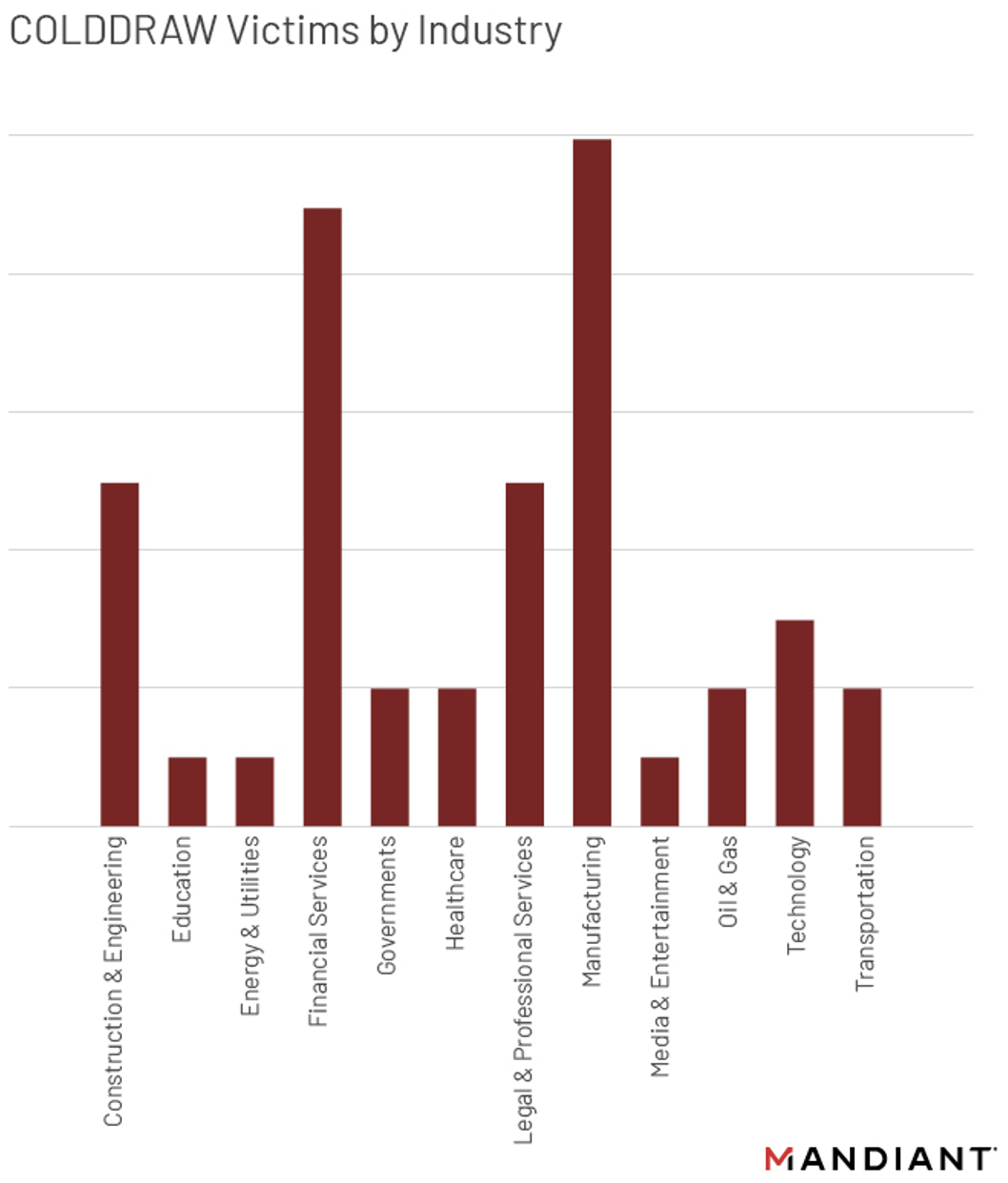
Other Malwares
Wedgecut is a programme that runs under the name “check.exe.” It’s a reconnaissance tool that uses PowerShell to enumerate the Active Directory.
Bughatch is a C&C server downloader that retrieves PowerShell scripts and files. To avoid detection, it loads in memory from a remote URL. Burntcigar is a tool that uses a weakness in an Avast driver to terminate processes at the kernel level.
Termite is a memory-only dropper that downloads and loads the payloads mentioned above. However, various threat groups have used this technology in their campaigns. This indicates that it is not exclusive to Cuban threat actors.
Ransomware Operations
Threat actors use stolen account credentials obtained with the widely available Mimikatz and Wicker tools to escalate privileges. They then use Wedgecut to undertake network reconnaissance before using RDP, SMB, PsExec, and Cobalt Strike to migrate laterally.
The next deployment is Termite-loaded Bughatch and followed by Burntcigar. Deactivating security mechanisms paves the way for data exfiltration and file encryption.
The Cuban gang does not employ any cloud services for the data exfiltration process. Instead, they use their private network for routing.
End Note
In May 2021, the Cuba ransomware teamed up with the spammers behind the Hancitor malware. They used DocuSign phishing emails to try to obtain access to company networks. Since then, Cuba’s activities have focused on weaknesses in public-facing systems.
The attacks have become more potent as a result of this change. At the same time, it’s easier to stop it because security patches to fix the exploited flaws have been available for months. The Cuba operation will then most likely shift its focus to other weaknesses.
IOCs
| MALWARE FAMILY | Indicator |
| TERMITE/BEACON | irrislaha[.]com |
| BEACON | leptengthinete[.]com |
| BEACON | siagevewilin[.]com |
| BEACON | surnbuithe[.]com |
| TERMITE | 64.235.39[.]82 |
| BEACON | 64.52.169[.]174 |
| Suspect certificate | 144.172.83[.]13 |
| BEACON | 190.114.254[.]116 |
| BEACON | 185.153.199[.]164 |
| TERMITE | 45.32.229[.]66 |
| BEACON | 23.227.197[.]229 |
| Packer imphash | 2322896bcde6c37bf4a87361b576de02 |
| Packer cert CN | FDFWJTORFQVNXQHFAH |
| Packer cert md5 | 5c00466f092b19c85873848dcd472d6f |


[…] Cuban Ransomware hacks Microsoft Exchange Servers […]