The U.S. Department of State, the U.S. Department of the Treasury, and the Federal Bureau of Investigation issued a joint advisory to alert the international community, the private sector, and the public to attempts by the Democratic People’s Republic of Korea (DPRK) and remote DPRK information technology (IT) workers to obtain employment while posing as non-DPRK nationals.
The advisory is intended to provide freelance recruitment and digital payment platforms, along with private sector companies that may intentionally or inadvertently recruit, hire, or facilitate the hiring of DPRK IT workers, with information and tools to counter the risks associated with these activities.
Hiring or supporting the activities of DPRK IT workers poses many risks, ranging from theft of intellectual property, data, and funds to reputational harm and legal consequences, including sanctions under both United States and United Nations authorities.
The advisory provides detailed information on how DPRK IT workers operate and identifies red flags to help companies avoid hiring them and identify those who may already be abusing their services. Additionally, it provides information about relevant United States and United Nations sanctions, including a non-exhaustive list of activities for which persons could be sanctioned by the U.S. government.
Targets include financial, health, social media, sports, entertainment, and lifestyle-focused companies located in North America, Europe, and East Asia, with most of the dispatched workers situated in China, Russia, Africa, and Southeast Asia.
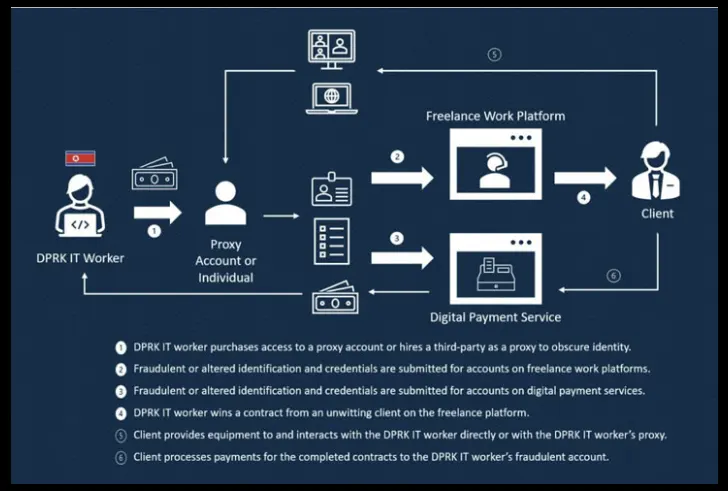
Besides deliberately obfuscating their identities, locations, and nationality online by using VPNs and misrepresenting themselves as South Korean citizens, potential red flags indicating the involvement of DPRK IT workers are as follows –
- Multiple logins into one account from various IP addresses in a short period
- Logging into multiple accounts on the same platform from one IP address
- Logged into accounts continuously for one or more days at a time
- Use of ports such as 3389 that are associated with remote desktop sharing software
- Using rogue client accounts on freelance work platforms to boost developer account ratings
- Multiple developer accounts receiving high ratings from one client account in a short time
- Frequent money transfers through payment platforms to China-based bank accounts, and
- Seeking payment in virtual currency
In one instance highlighted in the advisory, North Korean developers working for an unnamed U.S. company carried out an unauthorized theft of over $50,000 in 30 small installments without the firm’s knowledge over the course of several months.
Related reading: Recently in one of our blog posts, we told you how Windows updates are being used to deliver North Korean Malwares
If you like our blogposts and would like to show your love, then we would highly appreciate your kind comments and shares on social media like linkedIn. Do subscribe! Thanks!

