The rapid shift to remote work in spring of 2020 presented a fresh opportunity for threat actors to subvert traditional defense-in-depth protections by targeting the weakest points of the new network perimeter — devices which are routinely purchased by consumers but rarely monitored or patched — small office/home office (SOHO) routers.
Actors can leverage SOHO router access to maintain a low-detection presence on the target network and exploit sensitive information transiting the LAN. Black Lotus Labs, the threat intelligence arm of Lumen Technologies, is currently tracking elements of what appears to be a sophisticated campaign leveraging infected SOHO routers to target predominantly North American and European networks of interest.
A novel multistage remote access trojan (RAT) that’s been active since April 2020 is exploiting known vulnerabilities to target popular SOHO routers from Cisco Systems, Netgear, Asus and others.
The malware, dubbed ZuoRAT, can access the local LAN, capture packets being transmitted on the device and stage man-in-the-middle attacks through DNS and HTTPS hijacking, according to researchers from Lumen Technologies’ threat-intelligence arm Black Lotus Labs.
The ability to not only hop on a LAN from a SOHO device and then stage further attacks suggests that the RAT may be the work of a state-sponsored actor, they noted in a blog post published Wednesday.
Lumen says, “While we currently have a narrow view of the full extent of the actor’s capabilities due to the limited state of SOHO device monitoring in general, using proprietary telemetry from the Lumen global IP backbone, Researchers have enumerated some of the command-and-control (C2) infrastructure associated with this activity and identified some of the targets. Researchers assess with high confidence the elements we are tracking are part of a broader campaign.”
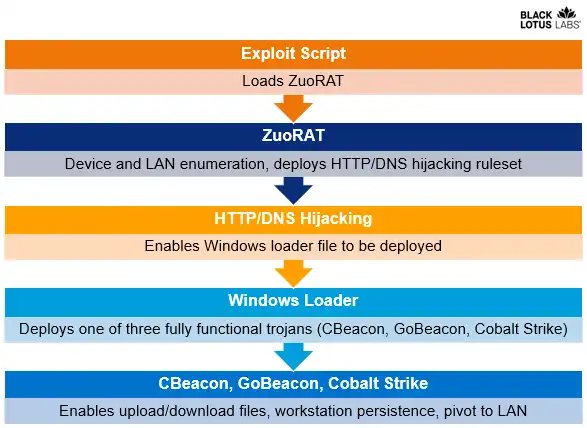
ZuoRAT Router Malware Overview
The ZuoRAT agent framework enables in-depth reconnaissance of target networks, traffic collection and network communication hijacking. It can be divided into two components: the first included functions that would auto-run upon execution of the file. The second component was comprised of functions that were embedded into the file but were not explicitly called. Researchers assess that these functions were intended to be called by additional commands. ZuoRAT appears to be a heavily modified version of the Mirai malware.
Recommendations
Though advanced actors have long demonstrated the capability and intent to target sensitive networks, the industry has uncovered only a handful of router-based malware specifically designed to covertly target them. The sudden shift to remote work spurred by the pandemic allowed a sophisticated adversary to seize this opportunity to subvert the traditional defense-in-depth posture of many well-established organizations. The capabilities demonstrated in this campaign – gaining access to SOHO devices of different makes and models, collecting host and LAN information to inform targeting, sampling and hijacking network communications to gain potentially persistent access to in-land devices and intentionally stealth C2 infrastructure leveraging multistage siloed router to router communications – points to a highly sophisticated actor that researchers hypothesize has been living undetected on the edge of targeted networks for years.
Black Lotus Labs has added the IoCs from this campaign into the threat intelligence feed that fuels the Lumen Connected Security portfolio, and researchers continue to monitor for new infrastructure, targeting activity and expanding TTPs. Researchers will continue to collaborate with the security research community to share findings related to this activity and ensure the public is informed. Researchers encourage the community to monitor for and alert on these and any similar IoCs.
Researchers also advise the following:
- Network defenders: Use IoCs outlined in this report to monitor for the Windows loader and its modules, as well as connections to any suspicious infrastructure.
- Consumers with SOHO routers: Users should follow best practices of regularly rebooting routers and installing security updates and patches. Users should leverage properly configured and updated EDR solutions on hosts and regularly update software consistent with vendor patches where applicable.
- Researchers recommend that businesses consider comprehensive Secure Access Service Edge (SASE) or similar solutions to bolster their security posture and enable robust detection on network-based communications.

