Researchers from the security firm Kloudle discovered security flaws in Google’s web application firewall’s default protection. This flaw allowed the company’s cloud-based safeguards to be circumvented.
The researchers were able to circumvent the web app firewalls of both Google Cloud Platform (GCP) and Amazon Web Services (AWS) by sending a POST request larger than 8KB in size.
According to Kloudle, “The default behaviour of Cloud Armor in this situation may allow malicious requests to evade Cloud Armor and directly access an underlying application.”
Use of WAF
Web application firewall suites add an important layer of protection to modern web applications. Even if the underlying application is susceptible, WAF can defend them from a wide range of threats such as code execution, SQL injection, cross-site scripting, and so on.
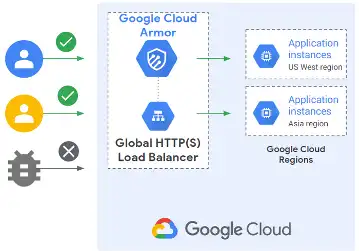
Cloud Armor
Google’s Cloud Armor WAF includes a collection of preset firewall rules based on the free source OWASP ModSecurity Core Rule Set. Cloud Armor supports the creation of custom rule expressions, as well as a set of pre-configured web application firewall rules based on the OWASP ModSecurity Core Rule Set.
GCP clients can use Cloud Armor to safeguard apps served by Google Cloud Load Balancing. Users can mitigate the risk by establishing a custom Cloud Armor rule to reject HTTP requests with request bodies greater than 8192 bytes. It is a generic rule that can be further customised to permit specific exceptions.
Explaining the 8KB limitation and vulnerability
Cloud Armor’s web application firewall inspects incoming HTTP requests and compares them to user-defined rule-based regulations. Based on the rules triggered by a specific request, the Cloud Armor service can be configured to allow or reject a request to the underlying application.
Cloud Armor’s web application firewall features a non-configurable HTTP request body size limit of 8 KB. This indicates that Cloud Armor will only examine the first 8192 bytes or characters of the body of an HTTP POST request.
This is comparable to AWS’s web application firewall. However, in the case of Cloud Armor, the limitation is not as well recognised and is not as explicitly displayed to customers as it is in AWS. Furthermore, while configuring Cloud Armor rules using the web UI, clients are not offered a notification or notice.
This flaw can be exploited by sending an HTTP POST request with a body size larger than Cloud Armor’s 8 KB limit. Bypassing this safeguard, a potential attacker would be one-step closer to launching an assault on a web-hosted application.
Similar vulnerabilities in other cloud platforms
Kloudle chastised GCP for neglecting to alert customers about the problem. According to the researchers, other cloud-based WAFs have comparable drawbacks.
The Daily Swig asked Google and AWS to comment on Kloudle’s research and what security steps its cloud clients should take.
“This is part of continuing effort,” Kloudle told The Daily Swig. We have noticed request body limits with Cloudflare, Azure, and Akamai thus far. Some contain 8KB, while others have up to 128KB.”
A Kloudle spokesperson acknowledged the problematic security and functionality trade-offs cloud providers must make. They did, however, mention that cloud providers should do more to educate consumers about the risk.
“Perimeter security software is difficult to develop. “ I believe the 8KB limit permits them to reliably process other WAF rules in this scenario,” the employee added.
“They could do more to raise developer knowledge, such as making that rule default with the ability to disable it if desired.”
“According to the shared security responsibility paradigm, it is the end user’s responsibility to use the service safely,” they stated.
Endnote
Cloud Armor is a beneficial tool for protecting Google Cloud Platform resources and data; nevertheless, customers should be mindful of the limitations of its request filtering capabilities. Furthermore, they should take precautions to prevent any potential risk that may develop as a result of the 8 KB WAF constraint.

