Last year, hackers working for the Chinese government breached the computer networks of at least six state governments in the United States. Mandiant, a private cybersecurity business, announced the news on Tuesday in their report.
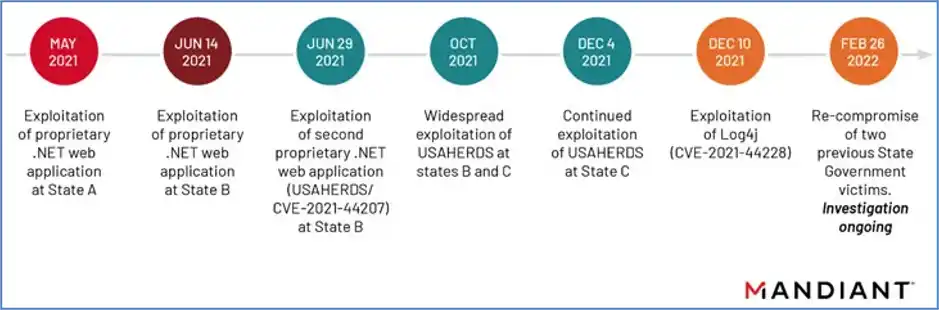
According to the allegations, APT41, a Chinese-affiliated state-sponsored threat actor, infiltrated at least six state government networks in the United States between May 2021 and February 2022. Hackers exploited insecure internet-facing web apps by retooling their attack vectors.
Vulnerabilities exploited by the attack
The exploited vulnerabilities included “a zero-day vulnerability in the USAHERDS programme as well as the now infamous zero-day in Log4j,” according to Mandiant analysts in a study published Tuesday, who described the attack as a “planned campaign.”
The ongoing attacks included the weaponization of exploits such as deserialization, SQL injection, and directory traversal vulnerabilities, in addition to web compromises, according to Mandiant.
The prolific advanced persistent threat, also known as Barium and Winnti, has a history of targeting organizations in both the public and private sectors in order to orchestrate espionage activity in tandem with financially driven operations.
During the attacks, an in-memory dropper dubbed DUSTPAN (aka StealthVector) was also spotted. This is orchestrated to execute the next-stage payload, as well as advanced post-compromise tools. The tools includes DEADEYE, a malware loader responsible for launching the LOWKEY implant.
Researchers observed a significantly increased use of Cloudflare services for command-and-control (C2) communications and data exfiltration among the many strategies, evasion methods, and capabilities utilised by APT41.
Motif behind the attacks on US
The Mandiant report does not identify the penetrated nations or provide a reason for the attacks, which began in May of last year. However, the Chinese group suspected of being behind the hacks, APT41, is known to start hacking operations for both traditional espionage and financial gain.
“The present crisis in Ukraine has deservedly captivated the world’s attention, and the potential for Russian cyber threats is clear. However we must remember that other significant threat actors throughout the world are continuing their operations as-usual,” said Geoff Ackerman, a principal threat analyst at Reston, Virginia-based Mandiant.
“We cannot let other cyber activity to fall by the wayside, especially given our observations that this campaign from APT41, one of the most prolific threat actors globally, continues to this day,” he said in his statement.
Even though the Biden administration has announced further procedures to protect federal government networks from hacking, state entities remain prime targets for hackers. This is an especially pressing worry in light of the enormous SolarWinds espionage campaign, in which Russian intelligence operatives exploited supply chain flaws to breach the networks of at least nine US agencies and scores of private-sector organisations.
About APT41
The gang was linked to a global penetration effort that used a number of exploits in early 2020. Citrix NetScaler/ADC, Cisco routers, and Zoho ManageEngine Desktop Central were used to launch malicious payloads against dozens of businesses in 20 countries.
The operations of APT41 were originally outlined in detail in a report by cybersecurity firm FireEye. Because of its twin concentration on espionage and financial crimes, the hacker outfit was dubbed ‘Double Dragon.’
The paper outlines a history of supply chain attacks on software developers that began in 2014. APT41 hackers were also able to introduce harmful code into video game files sent by legal game distributors.
The efforts of the cyber gang eventually garnered the attention of US officials. The Department of Justice charged five members of APT41 in 2019 and 2020, putting them on the FBI’s cyber most wanted list.
While APT41 has been tied to both financial crime and espionage, Mandiant researchers believe the latter is the goal in this most recent case.
Endnote
The current leak continues APT41’s habit of immediately exploiting freshly published vulnerabilities like Log4Shell to obtain early access to target networks. Within hours of the information being public, the targeted networks included two U.S. state governments, as well as insurance and telecommunications companies.
If anything, the new operations are evidence of a continually evolving enemy capable of adjusting its goalposts as well as refining its malware arsenal to hit enterprises of strategic interest around the world.

