- Cisco Talos has observed a new Transparent Tribe campaign targeting Indian government and military entities. While the actors are infecting victims with CrimsonRAT, their well-known malware of choice, they are also using new stagers and implants.
- This campaign, which has been ongoing since at least June 2021, uses fake domains mimicking legitimate government and related organizations to deliver malicious payloads, a common Transparent tribe tactic.
- Based on our analysis of Transparent Tribe operations over the last year, the group has continued to change its initial entry mechanisms and incorporate new bespoke malware, indicating the actors are actively diversifying their portfolio to compromise even more victims.
- Notably, the adversary has moved towards deploying small, bespoke stagers and downloaders that can be easily modified, likely to enable quick and agile operations.
APT Profile
Transparent Tribe is a suspected Pakistan-linked threat actor. This group targets individuals and entities associated with governments and military personnel in the Indian subcontinent, specifically Afghanistan and India. Transparent Tribe has also been known to use their CrimsonRAT implant against human rights activists in Pakistan.
The group primarily uses three Windows-based malware families to carry out espionage activities against their targets.
- CrimsonRAT is a .NET-based implant that has been the group’s malware of choice since at least 2020 . Transparent Tribe’s multiple campaigns leveraging CrimsonRAT over the years indicate a steady evolution in the implant’s capabilities.
- ObliqueRAT is a C/C++-based implant discovered by Talos in early 2020. ObliqueRAT is primarily reserved for highly targeted attacks on government personnel and in operations where stealth is a prime focus of the attackers’ infection chain. This implant has also seen a constant evolution in deployment tactics and malicious functionalities over time.
- Custom malware used by Transparent Tribe consists of easily and quickly deployable downloaders, droppers and lightweight RATs containing limited capabilities as opposed to CrimsonRAT and ObliqueRAT.
Transparent Tribe also maintains a suite of mobile implants in their arsenal. Implants such as CapraRAT are constantly modified to be deployed against targets. These implants contain a plethora of malicious capabilities meant to steal data from mobile devices.
Threat
Transparent Tribe, also known as APT36 and Mythic Leopard, continues to create fake domains mimicking legitimate military and defense organizations as a core component of their operations. In the latest campaign conducted by the threat actor, Cisco Talos observed multiple delivery methods, such as executables masquerading as installers of legitimate applications, archive files and maldocs to target Indian entities and individuals.
Transparent Tribe uses phishing to deliver maldocs and malicious web domains to push its malware, which is primarily Windows-based. The fake websites used to deliver payloads mimic government and defense organizations and will serve visitors downloader executables, packaged up to appear to be friendly software, .PDFs, or image files.
While past themes have included topics such as COVID-19, the APT moves with the times and adapts to different trends. The latest samples, deployed in 2022, include a fake version of Kavach, a multi-factor authentication (MFA) application.
Talos says that the legitimate Kavach app is “widely used” by India’s military for accessing government resources. If a target executes the fake .NET executable, upon installation, a legitimate version of the app is installed — alongside a malware dropper.
The second version of this infection vector might raise suspicion, though, as the full MSI installer for Kavach is pulled — as a 141MB package.
Malicious payloads, including the Remote Access Trojan (RAT) CrimsonRAT are downloaded and executed.
Since 2020, the .NET RAT is considered the APT’s “malware of choice” and is capable of extensive data theft and surveillance. However, Talos notes that Transparent Tribe continues to “incorporate new bespoke malware, indicating the actors are actively diversifying their portfolio to compromise even more victims.”
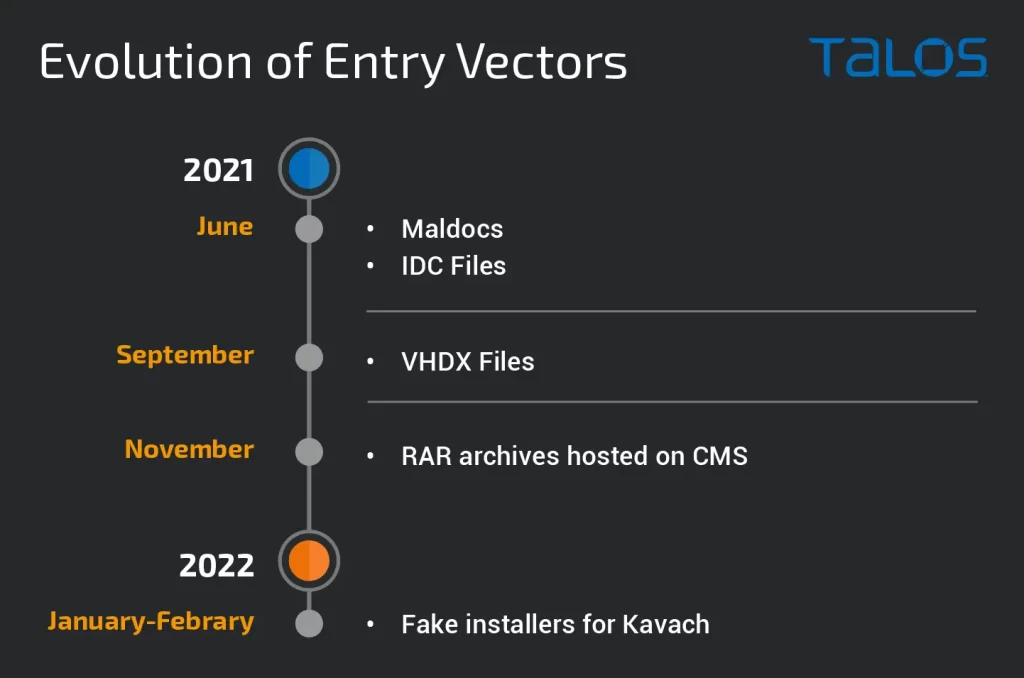
Entry Vectors
It is highly likely that Transparent Tribe used spearphishing emails to deliver download URLs for the archives to their targets via emails containing the passwords for the archives. As early as June 2021, the attackers primarily used malicious documents (maldocs) as an initial infection vector to deliver the malicious downloaders. This vector consisted of a malicious macro that would download and activate the downloader on the infected endpoint. This practice continued into July 2021.
Bottomline
As Talos recommends, Transparent Tribe has been a highly active APT group in the Indian subcontinent. Their primary targets have been government and military personnel in Afghanistan and India. This campaign furthers this targeting and their central goal of establishing long term access for espionage. The use of multiple types of delivery vehicles and file formats indicates that the group is aggressively trying to infect their targets with their implants such as CrimsonRAT. They have continued the use of fake domains masquerading as government and quasi-government entities, as well as the use of generically themed content-hosting domains to host malware. Although not very sophisticated, this is an extremely motivated and persistent adversary that constantly evolves tactics to infect their targets.
Organizations should remain vigilant against such threats, as they are likely to proliferate in the future. In-depth defense strategies based on a risk analysis approach can deliver the best results in the prevention. However, this should always be complemented by a good incident response plan which has been not only tested with tabletop exercises and reviewed and improved every time it’s put to the test on real engagements.
If you would like to hear about the latest on cybersecurity, subscribe to our newsletter, follow us on LinkedIn and share the informative articles with your followers on social media.

