Recently a group of hackers from North Korea are actively targetting small and mid-size businesses with new ransomware popularly known as H0lyGh0st. They are reportedly continuing these cyberattacks on the businesses since September 2021. Microsoft Threat Intelligence Center (MSTIC) has found them to be active since June 2021 and their original name was DEV-0530. They have adopted a new fanatic name – “H0lyGh0st” and carrying out the cyber attacks with a ransomware of the same name.
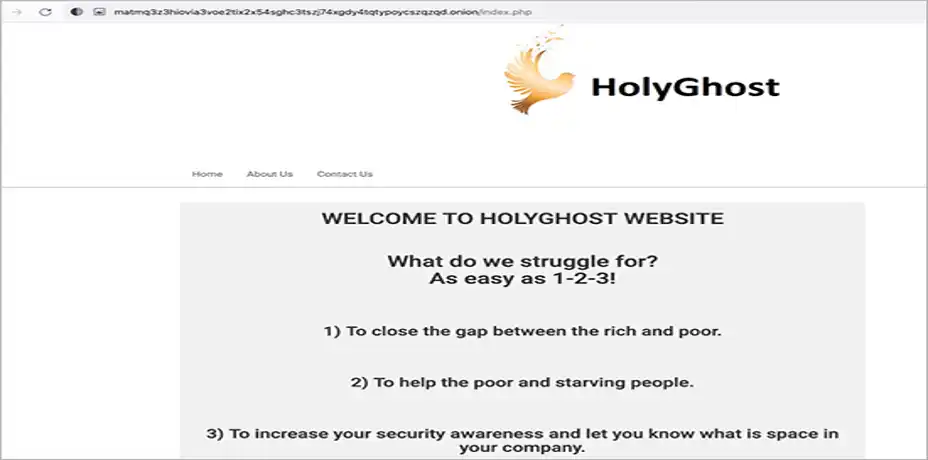
Intelligence has found a site named .onion, where these attackers interact with their future victims.
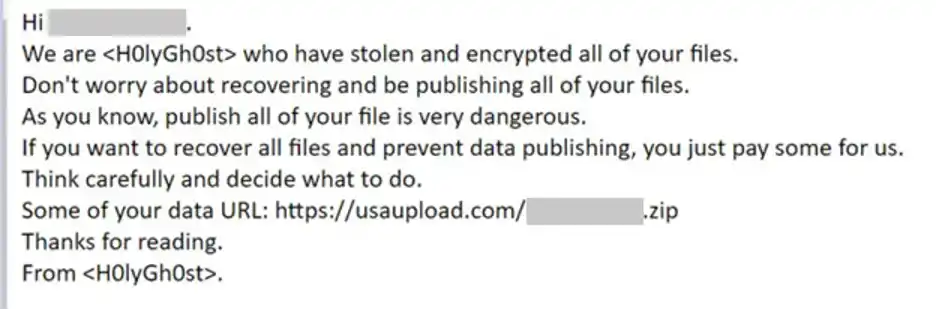
The basic process of their hacking is to encrypt the files present on the remote device and use extension .h0lyenc and send the owner a specimen of the files as proof. And, before restoring access to files, they ask for payment in Bitcoins. These jocks sometimes also threaten the victims to publish their data online if the victim refuses to pay.
The ransom demands are reported to be between 1.2 to 5 bitcoins. Though, the hacker’s cryptocurrency wallet shows no successful ransom payments from the victims since July 2021.
They are reportedly targetting small to medium businesses like banking sectors, schools, and event management companies.
Researchers have found them to be linked with another North-Korean-based gang, tracked as PLUTONIUM(aka Andariel or DarkSeoul). PLUTONIUM is a sub-group working under the Lazarus umbrella or Hidden Cobra. This group has also been found to use the same ransomware as the DEV-0530s in their campaigns. MSTIC has also found DEV-0530 using the hacking tools, created alone by PLUTONIUM.
Who are DEV-0530s?
It is a group of people claiming that they help the needy and poor.
The MSTIC’s Analysts found them to use the same tactics as another ransomware family, GoodWill, and claim to “bridge the gap between the poor and rich”, in their dark web portal, .onion. Secondly, they say proudly that “this all is done to help the people who are starving and in need of money.”
They generally send the victims with ransom notes having a link to their .onion site.
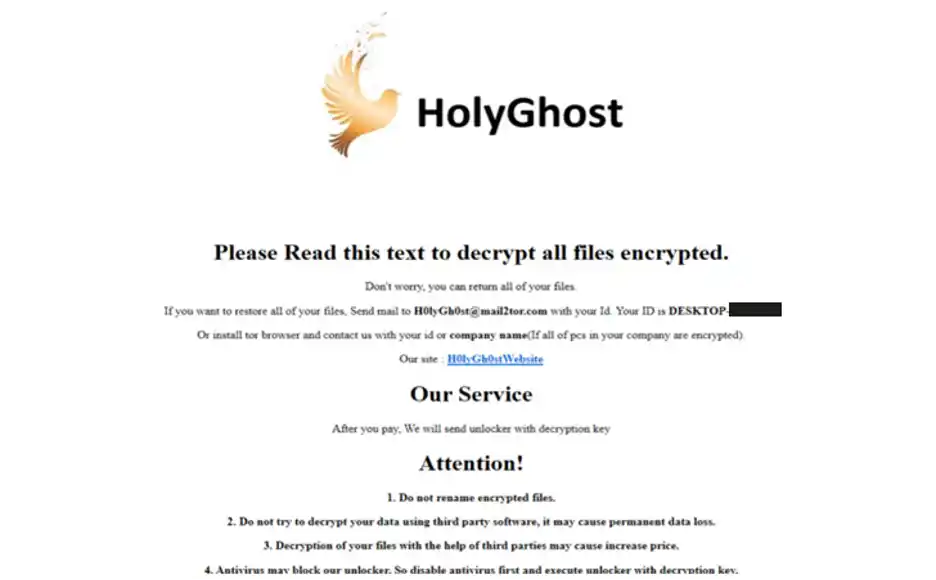
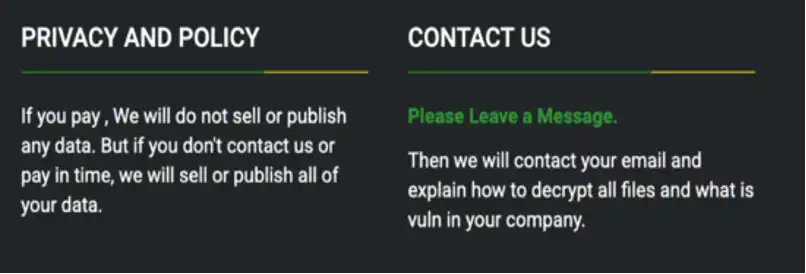
They have been found to send a very humble note to the victims asking them to pay the ransom amount and after that, they would send the decryption keys for the encrypted files. Just like the one below in this picture.
In their third claim, they justify their work as to “increase the victim’s security awareness and let her/him know their space in their company”
Like most of the other ransomware jocks, DEV-0530 claims in their website’s privacy policy that they will display the victim’s content online unless they get paid. They even provide a contact form online for the victims to get in touch with them.
Technical Background of the H0lyGh0st
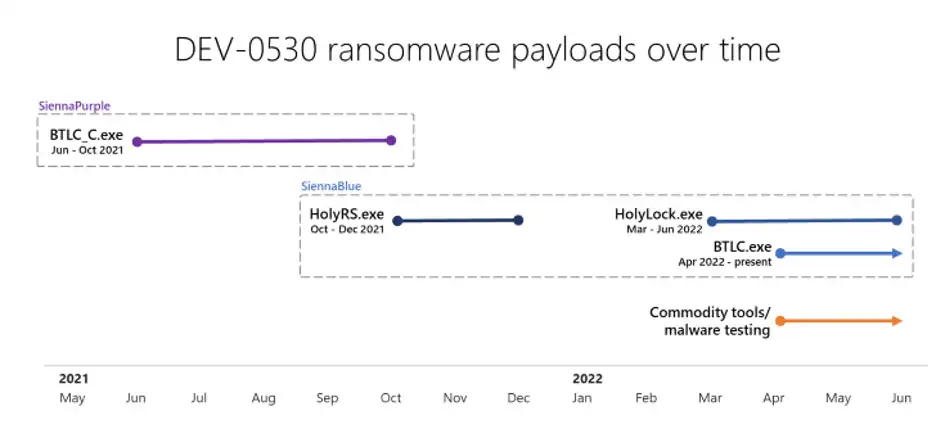
Four different variants of the H0lyGh0st ransomware are found by the researchers between June 2021 and May 2022. These target Windows systems and are named: BTLC_C.exe, HolyRS.exe, HolyLock.exe, and BLTC.exe.
BTLC_C.exe (aka SiennaPurple) is written in C++, and the other three (dubbed SiennaBlue) are coded in Go.
It is reported that some newer strains are also being developed with changes in their core functionality. They would be able to delete scheduled tasks and also remove them from the affected devices if necessary.
Some more ransomwares like Black Basta, Black Cat and Vice Society have also emerged lately carrying out the cybercrimes across the globe.
Why Ransomware attacks are common in North Korea?
The MSTIC Analysts came to the two reasons after observing the North Korean geopolitical systems and circumstances:
1) The North Korean economy has shattered since 2016 due to natural disasters, sanctions, and droughts. The 2020 Covid lockdown even pushed this to higher levels. So, the North Korean government might be sponsoring these cyberattacks on banks and schools through cryptocurrency wallets for the last five years.
2) Individuals involved in this might be using the PLUTONIUM tools for their gains.
But yet they are not certain of the actual reason and this raises the need for increased cyber-security awareness amongst the general public.
To know more about the rising cybercrimes in North Korea click here.
Recommended Customer Security Actions:
MSTIC researchers suggested some security patches that one can use to prevent these attacks as below:
1) Use Multi-Factor Authentication (MFA) on all your accounts, devices, and drives at all times and locations.
2) Enable passwordless authentications such as Microsoft Authenticator, FIDO Keys, Windows Hello, etc.
3) Disable legacy authentication
While small and medium businesses can use the below features for protection against them:
1) Always keep tampering protection on, so that attackers cannot stop the security services.
2)Enforce network protection to keep yourself safe from being trapped on malicious domains and websites.
3) Use device discovery mode to increase the chances of finding the lost devices and onboarding them back on your Microsoft Defender.
Written By: Ankita Anand
Editor: Robin
Found this blog interesting then please follow cybermetrics.eu .

