In the fourth quarter of 2021, there was a lot of activity in the ransomware space. Threat analysts discovered 722 distinct assaults with 34 distinct versions.
This flurry of activity complicates matters for the defenders, making it difficult to keep track of individual group tactics, indicators of compromise, and detection opportunities.
Increasing Attacks
The latest quarter witnessed an 18% increase in assault volume when compared to the third quarter of 2021. Meanwhile, the comparison to Q2 2021 results in a 22% difference, indicating a pattern of growing attack numbers.
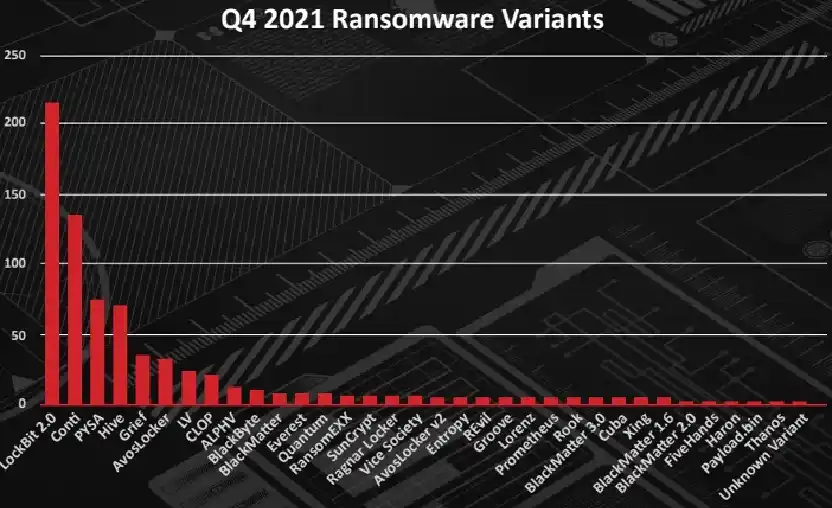
According to Intel 471, the most common ransomware groups in the fourth quarter of 2021 were LockBit 2.0 (29.7 %), Conti (19 %), PYSA (10.5 %), and Hive (10.1 % ).
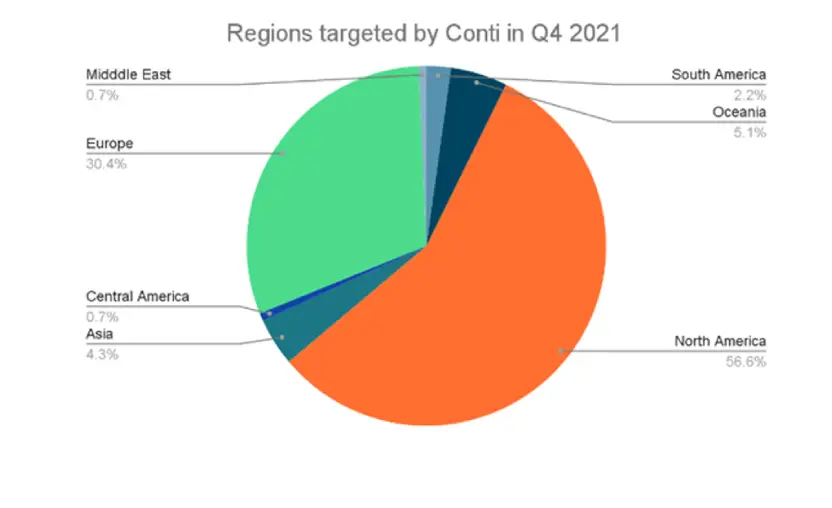
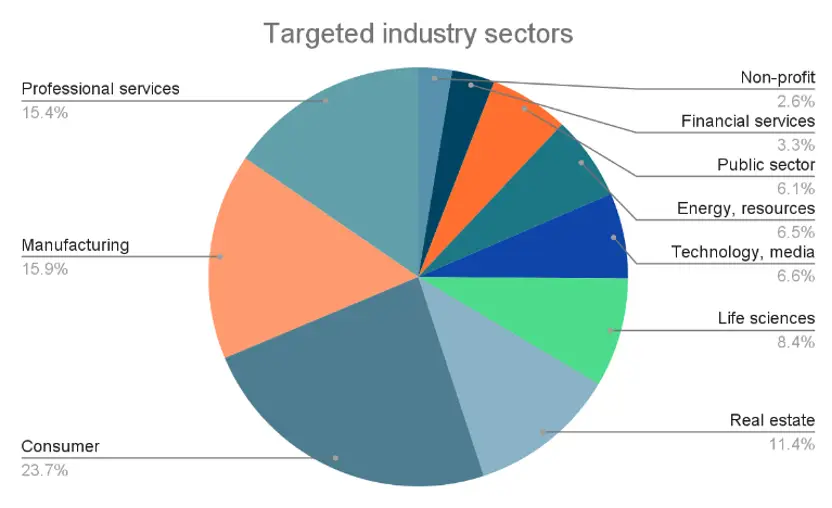
Almost half of all ransomware attacks targeted North America, followed by Europe (30%), and the rest of the world accounting for 20%. In terms of targeted sectors, attacks against consumer and industrial product sectors increased, accounting for one-fourth of all assaults in Q4 2021.
Growth-induced Changes
Only the Consumer and Industrial Products sector stands out, accounting for one out of every four assaults, according to the statistics for targeted industries. Manufacturing, professional services, and real estate all contributed significantly to the total.
When Q3 2021 data is compared to Q3 2021 data, the manufacturing sector has decreased while consumer and industrial products have increased. Furthermore, the fields of biological sciences and health care have grown tremendously.
This shift could be attributed to the increased profitability of associated goals as a result of the seasonal interest in shopping over the holidays and Black Friday/Cyber Monday.
Ransomware Attack Plan
Ransomware gangs have a tendency to interrupt business operations at the most inconvenient times. This is evidenced by a rise in attacks during the holiday season when corporations’ attention is directed to selling as many things as possible. Healthcare also takes on a more vital role as we approach the end of the year, potentially due to higher viral transmission rates in the northern hemisphere throughout the winter.
Consequently, firms are left vulnerable to attacks, as ransomware gangs actively seek any opportunity to get access to targeted enterprise networks. As a result, businesses must remain watchful and maintain their security systems up to date in order to be better prepared in the case of a ransomware attack on one of their infrastructures.
The FBI recently issued a warning that ransomware gangs frequently target corporations during mergers and acquisitions to create additional pressure during negotiations.
Risk Mitigation
Ransomware events can have a significant impact on business processes and cause firms to fail. Restoring data from an earlier recovery point can result in considerable loss of business transactions or other crucial data. Therefore, it is imperative that businesses take measures for risk mitigation.
- Backup your data, system images, and configurations, test them on a regular basis, and store the backups offline. Make certain that backups are tested on a regular basis and that they are not connected to the company network.
- Update and patch systems on a regular basis. This includes keeping operating systems, applications, and firmware secure.
- Put your incident response plan to the test. It enables you to detect plan shortcomings. Run through some basic questions and use the answers to create an incident response plan.
- Examine the work of your security team. To test the security of your systems and your ability to defend against a sophisticated assault, hire a third-party pen tester.
- Segment your networks. Ransomware assaults have recently shifted from stealing data to interrupting operations. It is critical that your corporate business functions and manufacturing/production operations are kept separate. Carefully filter and limit internet access to operational networks, identify links between these networks, and develop workarounds or manual controls to ensure that ICS networks can be isolated and continue to operate if your corporate network is compromised.
- Train employees. Email is still the most vulnerable attack vector for businesses. Users should be taught how to recognize and prevent phishing emails. Multi-factor authentication can aid in the prevention of unauthorized access to sensitive services.