Microsoft’s online store is actively distributing new spyware capable of managing social media accounts. This malware was discovered by Check Point Research (CPR). It is the research arm of cyber security software organisation Check Point. According to CPR, the malware has infected more than 5,000 active machines worldwide.
Electron bot is the name of the malware, and it is a modular SEO poisoning malware. SEO poisoning is the practice of attackers creating malicious websites and causing them to appear high in search engine rankings. Keyword stuffing and other black hat SEO techniques are used to accomplish this. It is used for social media promotion and click fraud. This malware has been discovered in 20 countries, with the majority of them being Russia, Bermuda, Spain, Sweden, and Bulgaria.
Electron gained access to Microsoft’s official shop by duplicating Temple Run and Subway Surfer games. The bot allows attackers to take control of infected computers. Except for a few minor alterations, the infected applications are indistinguishable from the originals on the Microsoft Store. Electron may be run from a distance, allowing operators to establish new accounts, log in, comment on, and like other social media posts in real-time.
The Infection
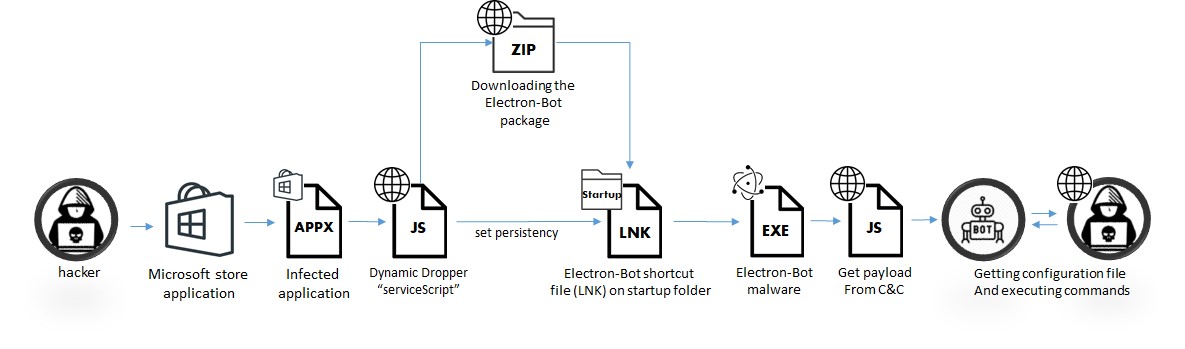
The infection begins when a victim downloads a malicious programme from the Microsoft Store. A JavaScript dropper is dynamically loaded when the app is activated, downloading and installing the malware.
When a user downloads and runs an infected programme or game, a malware dropper is dynamically loaded in the background from the attacker’s server. The dropper then performs a series of tasks, including downloading and installing malware that remains in the starting folder for a long time. When the system starts, the malware begins to function.
Malware Activity
According to researchers, the first indication that the attackers had gotten into Microsoft’s app store occurred towards the end of 2018. They identified an ad-clicker campaign hidden in an app called “Album by Google Photos,” according to reports.
Over time, malware has grown in size and strength. Electron, an open-source framework for creating cross-platform, native desktop apps using web technologies like JavaScript, inspired the bot’s name.
According to CPR, the bot hides by loading most of its controlling scripts dynamically from the attackers’ servers at run time. “This enables the attackers to modify the malware’s payload and change the bots’ behaviour at any time,” they added. According to them, this strategy keeps the virus flexible.
Once infected, the Electron bot engages in the following activities:
- The bot boosts the number of bad sites’ SEO rankings and is sold as a service to promote the rankings of other websites.
- It can be used as an ad clicker, clicking on distant websites in order to create clicks on ads and increase Pay-per-Click (PPC) ad revenue.
- Furthermore, the bot promotes online products to enhance a store’s sales rating or create PPC money.
- It promotes social media accounts to drive traffic to certain content. As a result, the view is obscured, resulting in more ad-clicking for the PPC kitty.
“Because the bot’s payload is loaded dynamically at each run time,” they explained, “assailants can tweak the code and change the bot’s behaviour to high-risk.” “They may, for example, start a second stage and distribute additional malware, such as ransomware. This can all take place without the victim’s knowledge”, CPR stated.
Endnote
The attackers have yet to be identified, but CPR suspects they may be from Bulgaria. The bot is employed to advertise numerous Bulgarian social media accounts and products; therefore, it got to this conclusion. Despite not being deployed to participate in high-risk actions, the bot’s powers and adaptability make it a continuous threat. CPR advises users to be cautious when downloading software from the Microsoft Store.
IOCs
Executables:
- f2a97841d58aa9050b2275302be6aa78
- 240e9adca3695da4ba177c0238141881
- 33145894a81fd3f6fde4f528630b1f7a
Zipped folders:
- 8720d6cefd71ef30c3fe66965fea841a
- 0a919ab3c63608e00290c9d4d4eb3a01
- 07ebca17e1083461fbbe3376fe5ec1ed
- ec2c0a9be3ff2a922c02c9e1380eeabd
- 52c4990d30a8a7b560c57e775895ccad
Game publishers:
- Lupy games
- Crazy 4 games
- Jeuxjeuxkeux games
- Akashic games
- Goo Games
- Bizzon Case
C&C Domains:
- 11k[.]online
- Electron-Bot[.]s3[.]eu-central-1[.]amazonaws.com
Malware hosting sites:
- cdn[.]lupygames[.]com
- crazy4games-flash[.]s3[.]eu-west-1[.]amazonaws[.]com
- ytmp3[.]dog

